
On Monday, Apple released its first batch of publicly available “rapid security” patches, intended to quickly fix security vulnerabilities that are under active exploitation or pose significant risks to its customers.
According to the notice, the so-called rapid security response updates “deliver important security improvements between software updates.”
Rapid security responses were introduced to allow Apple customers to update their devices faster than a typical software update. Apple says the feature is enabled by default, and some quick patches can be installed without a reboot, but not always.
The express security update arrives for customers with iOS 16.4.1, iPadOS 16.4.1, and macOS 13.3.1. Once installed it will add a letter to the software version – such as iOS 16.4.1 (a), iPadOS 16.4.1 (a), macOS 13.3.1 (a). Users running older versions of Apple software will not receive the security hotfix. Apple said that the fixes will be included in subsequent software updates.
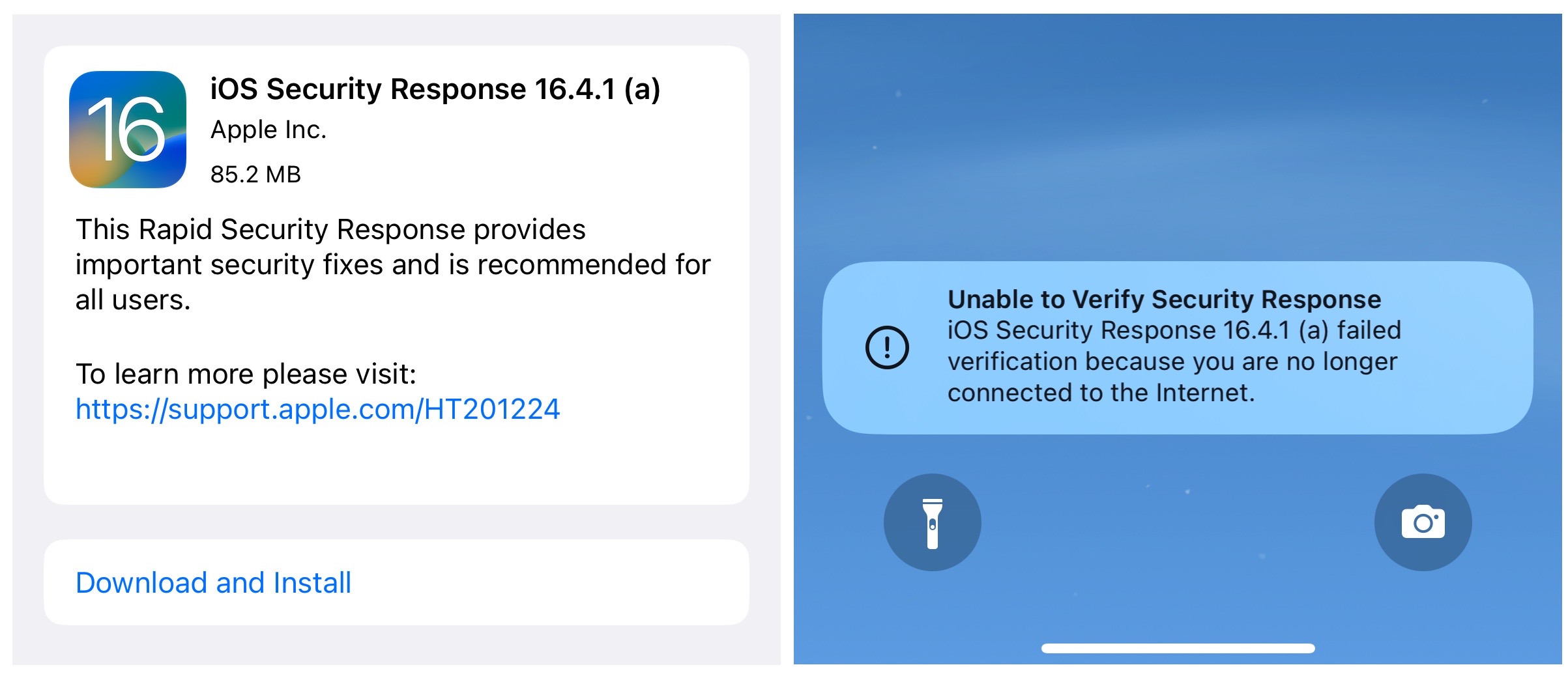
Image credits: TechCrunch (screenshot)
But Monday’s rollout wasn’t so smooth. Some customers said they couldn’t install the update. When tested by TechCrunch on iPhones, iPads, and Macs, the updates downloaded but didn’t install right away.
It’s also not clear what this security update fixes, and Apple did not respond to a request for comment.
In recent weeks, researchers have discovered new exploits developed by spyware makers QuaDream and NSO Group with the goal of targeting iPhone owners around the world. Both spyware makers exploited previously undisclosed vulnerabilities in Apple software that allowed their government agents to silently steal data from a victim’s device.
Citizen Lab said last month that Lockdown Mode, a feature Apple introduced last year to prevent similar targeted attacks, successfully blocked at least one vulnerability developed by NSO that abused a vulnerability in Apple’s smart home feature, HomeKit.
Given the apparent severity of this latest security patch, we’ll continue to try to update – as you should.
